获取证书过期时间脚本:
/etc/zabbix/scripts/check-cert-expire.sh:
#!/bin/bash
host=$1
port=$2
end_date=`/usr/bin/openssl s_client -servername $host -host $host -port $port -showcerts </dev/null 2>/dev/null |
sed -n '/BEGIN CERTIFICATE/,/END CERT/p' |
/usr/bin/openssl x509 -text 2>/dev/null |
sed -n 's/ *Not After : *//p'`
# openssl 检验和验证SSL证书。
# -servername $host 因一台主机存在多个证书,利用SNI特性检查
# </dev/null 定向标准输入,防止交互式程序。从/dev/null 读时,直接读出0 。
# sed -n 和p 一起使用,仅显示匹配到的部分。 //,// 区间匹配。
# openssl x509 -text 解码证书信息,包含证书的有效期。
if [ -n "$end_date" ]
then
end_date_seconds=`date '+%s' --date "$end_date"`
now_seconds=`date '+%s'`
echo "($end_date_seconds-$now_seconds)/24/3600" | bc
fi
域名自动发现脚本:
/etc/zabbix/scripts/sshcert_discovery.py
#!/usr/bin/env python
#coding:utf-8
import os
import sys
import json
#这个函数主要是构造出一个特定格式的字典,用于zabbix
def ssl_cert_discovery():
web_list=[]
web_dict={"data":None}
with open("/etc/zabbix/scripts/ssl_cert_list","r") as f:
for sslcert in f:
dict={}
dict["{#DOMAINNAME}"]=sslcert.strip().split()[0]
dict["{#PORT}"]=sslcert.strip().split()[1]
web_list.append(dict)
web_dict["data"]=web_list
jsonStr = json.dumps(web_dict,indent=4)
return jsonStr
if __name__ == "__main__":
print ssl_cert_discovery()
域名列表:
/etc/zabbix/scripts/ssl_cert_list:
www.baidu.com 443
www.qq.com 443
zabbix配置:
/etc/zabbix/zabbix_agentd.conf.d/userparameter_sslcert.conf
UserParameter=sslcert_discovery,/usr/bin/python /etc/zabbix/scripts/sshcert_discovery.py
UserParameter=sslcert.info[*],/bin/bash /etc/zabbix/scripts/check-cert-expire.sh $1 $2
在zabbix中添加模板:
Template_ssl_cert_info.xml
<?xml version="1.0" encoding="UTF-8"?>
<zabbix_export>
<version>3.0</version>
<date>2019-07-25T10:31:57Z</date>
<groups>
<group>
<name>Templates</name>
</group>
</groups>
<templates>
<template>
<template>Template ssl cert Information</template>
<name>Template ssl cert Information</name>
<description/>
<groups>
<group>
<name>Templates</name>
</group>
</groups>
<applications/>
<items/>
<discovery_rules>
<discovery_rule>
<name>ssl cert information</name>
<type>0</type>
<snmp_community/>
<snmp_oid/>
<key>sslcert_discovery</key>
<delay>10800</delay>
<status>0</status>
<allowed_hosts/>
<snmpv3_contextname/>
<snmpv3_securityname/>
<snmpv3_securitylevel>0</snmpv3_securitylevel>
<snmpv3_authprotocol>0</snmpv3_authprotocol>
<snmpv3_authpassphrase/>
<snmpv3_privprotocol>0</snmpv3_privprotocol>
<snmpv3_privpassphrase/>
<delay_flex/>
<params/>
<ipmi_sensor/>
<authtype>0</authtype>
<username/>
<password/>
<publickey/>
<privatekey/>
<port/>
<filter>
<evaltype>0</evaltype>
<formula/>
<conditions/>
</filter>
<lifetime>30</lifetime>
<description/>
<item_prototypes>
<item_prototype>
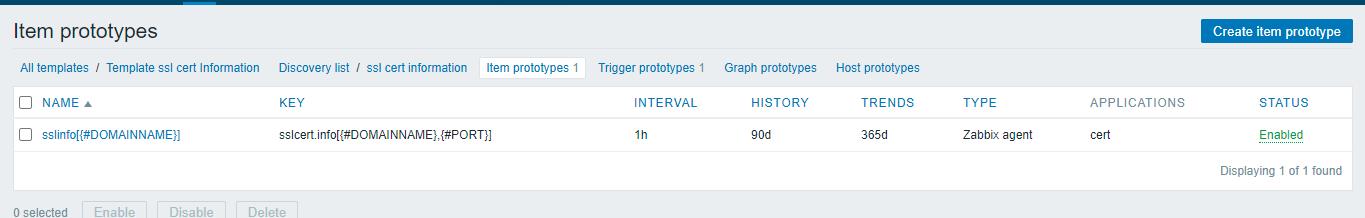
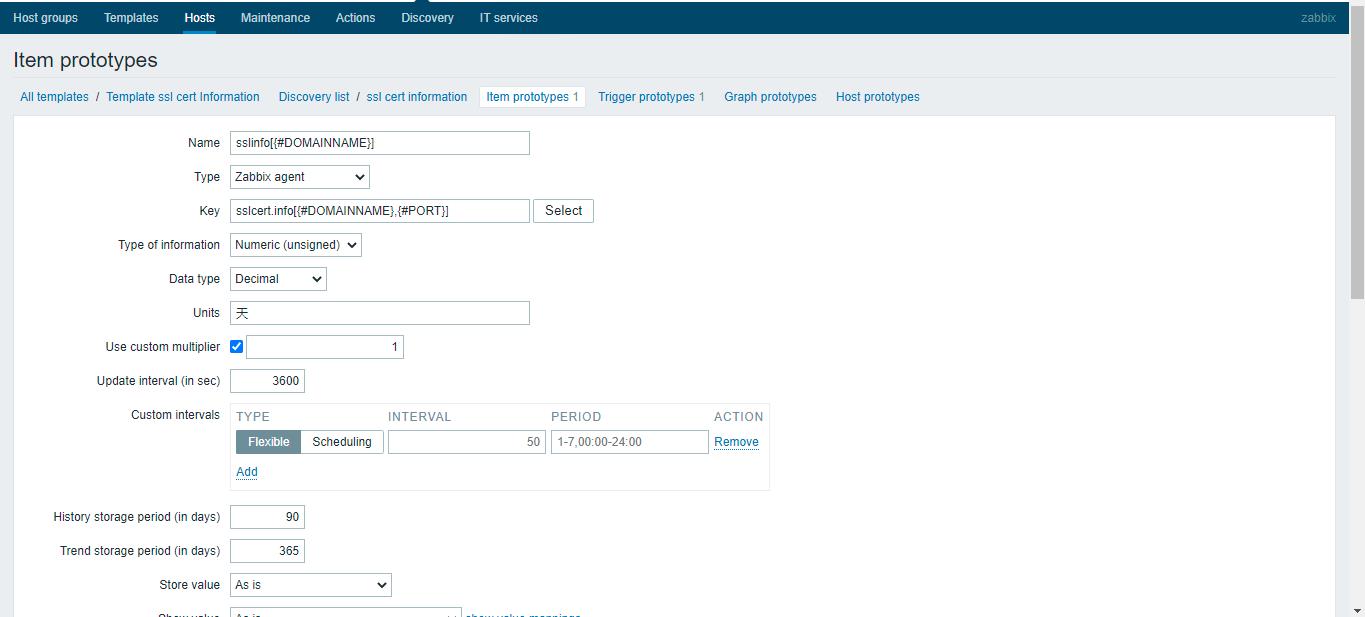
<name>sslinfo[{#DOMAINNAME}]</name>
<type>0</type>
<snmp_community/>
<multiplier>1</multiplier>
<snmp_oid/>
<key>sslcert.info[{#DOMAINNAME},{#PORT}]</key>
<delay>10800</delay>
<history>90</history>
<trends>365</trends>
<status>0</status>
<value_type>3</value_type>
<allowed_hosts/>
<units>天</units>
<delta>0</delta>
<snmpv3_contextname/>
<snmpv3_securityname/>
<snmpv3_securitylevel>0</snmpv3_securitylevel>
<snmpv3_authprotocol>0</snmpv3_authprotocol>
<snmpv3_authpassphrase/>
<snmpv3_privprotocol>0</snmpv3_privprotocol>
<snmpv3_privpassphrase/>
<formula>1</formula>
<delay_flex/>
<params/>
<ipmi_sensor/>
<data_type>0</data_type>
<authtype>0</authtype>
<username/>
<password/>
<publickey/>
<privatekey/>
<port/>
<description/>
<inventory_link>0</inventory_link>
<applications/>
<valuemap/>
<logtimefmt/>
<application_prototypes/>
</item_prototype>
</item_prototypes>
<trigger_prototypes>
<trigger_prototype>
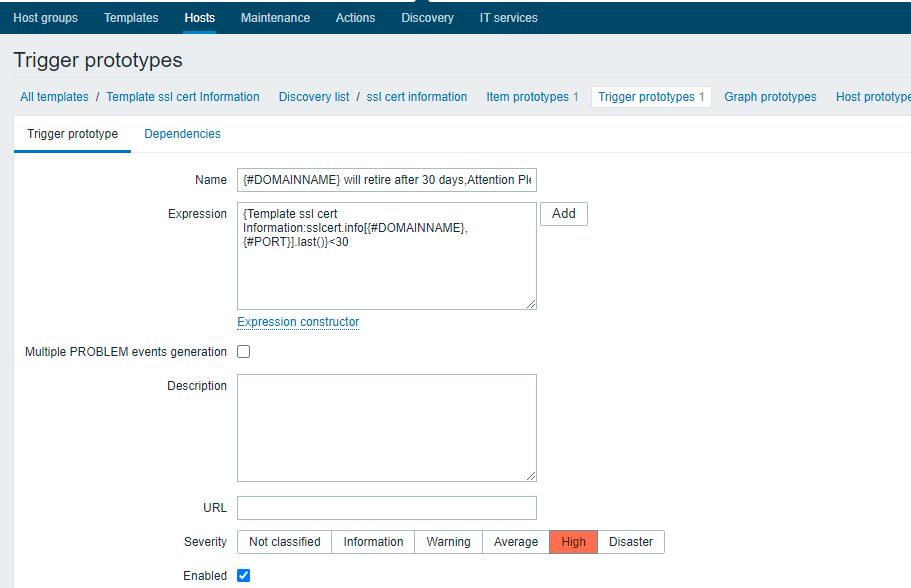
<expression>{Template ssl cert Information:sslcert.info[{#DOMAINNAME},{#PORT}].last()}<7</expression>
<name>{#DOMAINNAME} will retire after 7 days,Attention Please!</name>
<url/>
<status>0</status>
<priority>4</priority>
<description/>
<type>0</type>
<dependencies/>
</trigger_prototype>
</trigger_prototypes>
<graph_prototypes/>
<host_prototypes/>
</discovery_rule>
</discovery_rules>
<macros/>
<templates/>
<screens/>
</template>
</templates>
</zabbix_export>